EnOS™ APIM Security¶
EnOS APIM Definition¶
The EnOS API Management provides full lifecycle management services, which cover API creation, configuration, deployment, monitoring, open platform, and other capabilities, helping developers open data and services to applications via APIs. The are the main functions are as per the below.
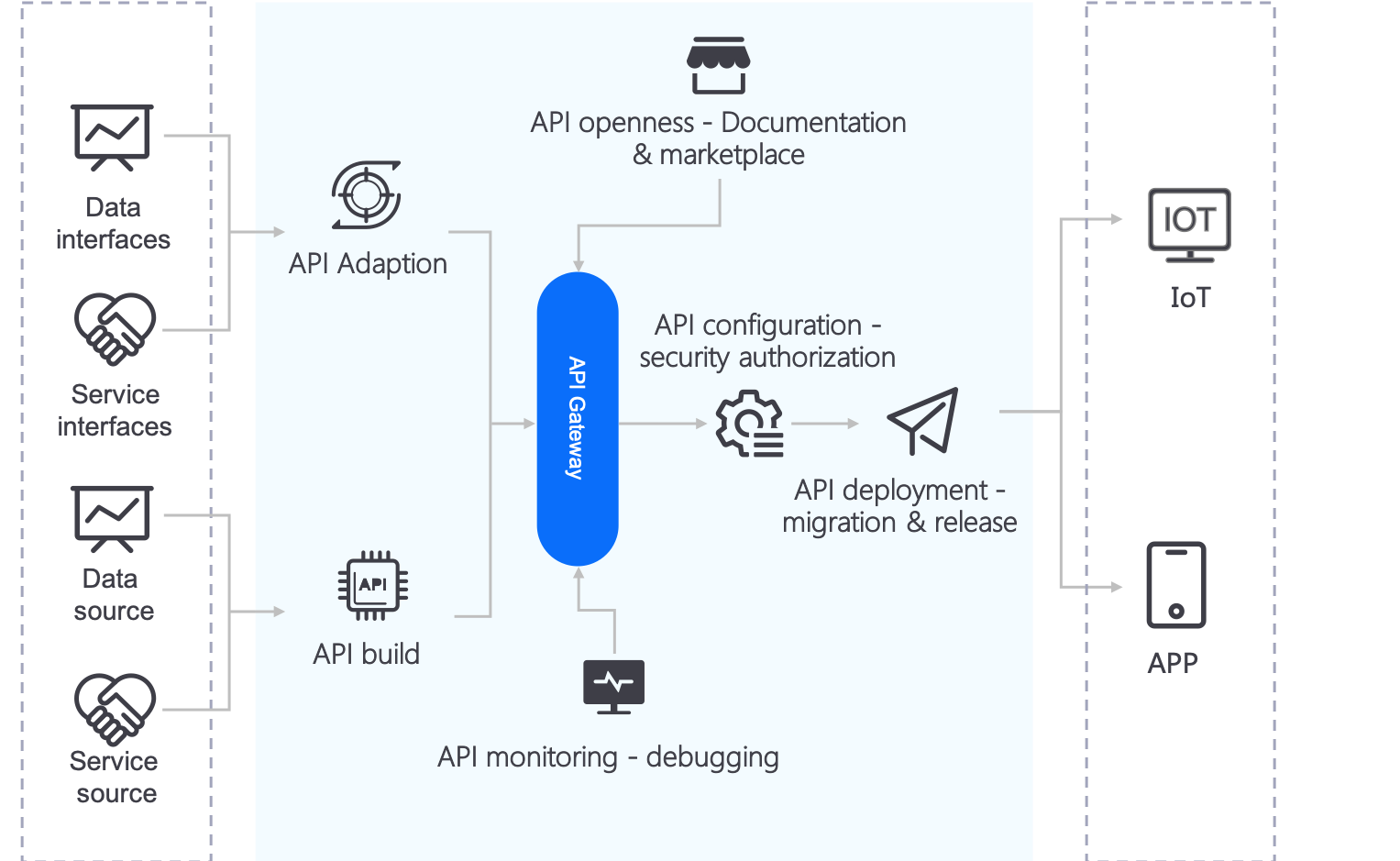
API creation: Provides the design, staging, hosting, and category management of APIs for API developers.
API configuration: Provides a rich set of configuration options, which helps to strengthen API security authorization, traffic limiting, log services, and other capabilities.
API deployment: Publishes and deploys APIs to multiple environments in a fast and convenient way.
API monitoring center: Ensures the stability of APIs at the service side through monitoring, analytics, pre-warning, and other capabilities.
API open platform: Links multiple parties to the APIM platform for API transactions, developing communities and training support, and establishing an open API economy.
EnOS APIM Security Rule¶
When developers open the services to external applications, they should first ensure the services, especially those related to the data lake, are secure so as to prevent malicious access to the company’s businesses. In order to do so, it is necessary to consider establishing communication links and the encryption, integrity, and non-repudiation of communication data, etc.
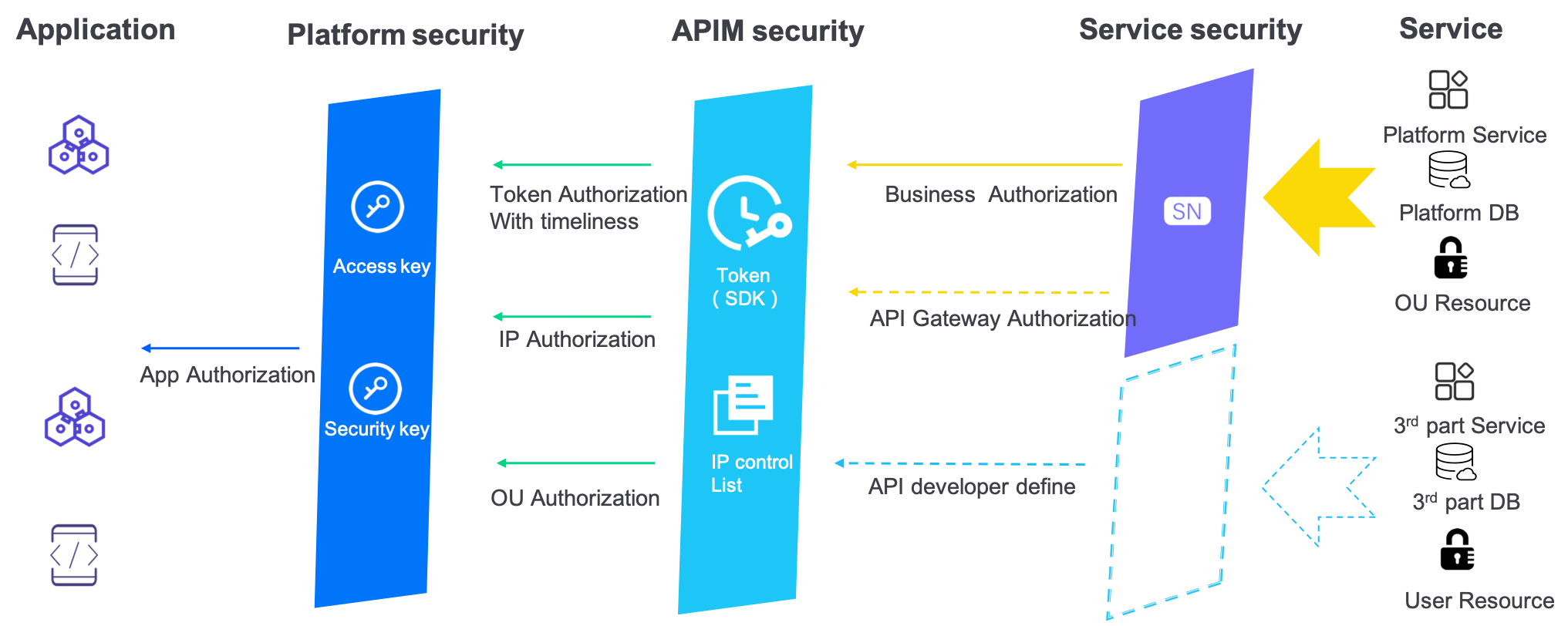
When the API request arrives at APIM, it needs to go through strict identity permission authentication to reach the back-end service. In general, APIM provides the following security authentication methods.
SA authentication: Uses the service account (SA), consisting of the application’s access key and access secret, for verification and authentication.
OU authentication: Provides
orgIdsymmetric encryption to verify whether the application request and background service are under the same OU permission.Token: Uses customized API token logic, which is mainly used to implement basic functions such as token issuance, token verification, token validity processing, token replacement, and so on.
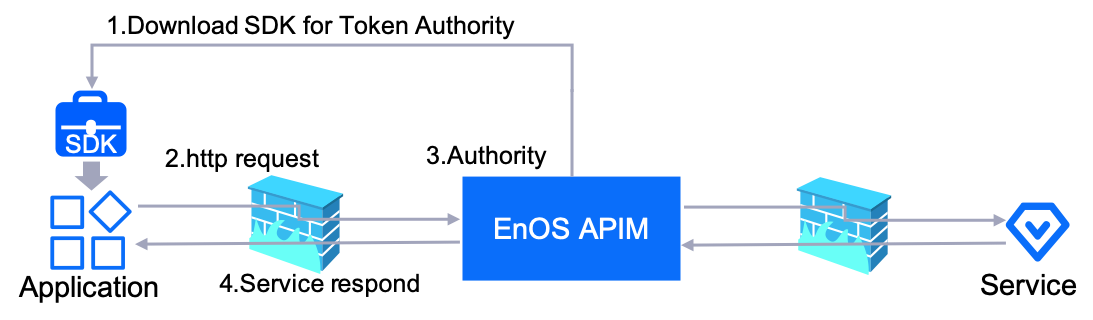
Currently, the APIM requires the caller to download an SDK for security authentication and integrate it into the application in order to verify the private key of the application through the security and timeliness of the token.
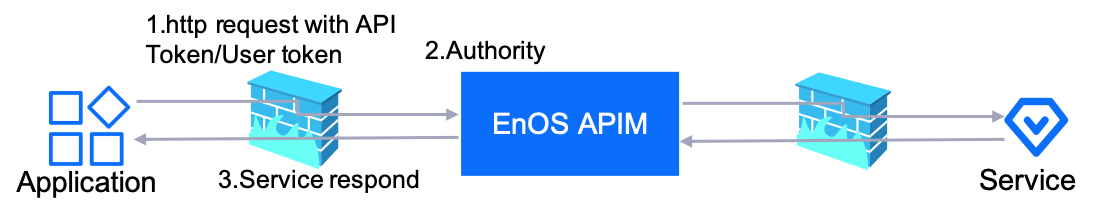
At present, you can generate an access token with the application access key, secret key, and system time stamp, and then use the access token to invoke EnOS APIs. You need to register an application on EnOS Management Console to get its access key and secret key, which are required as the values of the appKey and appSecret request parameters of the Get Access Token API.
The APIM provides the following access token functions.
Get Access Token: You can get the access token by providing a SHA256 encryption message containing the
appkey,timestamp, andappsecret. Access tokens, once gotten, will expire in 2 hours.Refresh Access Token: Before the expiry of an access token, you can refresh the token by providing the encryption message and the original access token.
Calling API with the access token: As long as you have a valid access token, you can call APIs with it by adding the below in the request header.
apim-accesstoken: The valid access token string.
apim-signature: A SHA256 encryption message that consist of the access token, query parameters, timestamp, and app secret.
IP control black and white list: The black and white list is also one of the basic functions of security protection. In fact, the core of it lies in judging the black and white lists of the IP addresses when the call is made.
In addition, when APIM routes requests to the backend, developers can also provide their own services and security authentication.
Customized encryption: The key mechanism of packet encryption is the secret key, which ensures security through asymmetric encryption or through the use of symmetrically encrypted business messages or key fields, or enhances security through white box encryption. This part involves many schemes and implementation methods, for which a separate article will be written.
API gateway permission: Any developer can request for API gateway permission control; in fact, this control is a background service under the relationship of 1 ~ N gateways, which can be used as an exclusive access permission to establish APIM.