Configuring Config Maps and Secrets¶
This section shows how the application developer can create new config maps and secrets to inject configuration information into the container.
Config maps can be used to store fine-grained information such as a single attribute, or coarse-grained information such as an entire profile or a JSON object. The config map can store key/value pair configuration data that can be used in pods. With config maps, it is easier to process strings that do not contain sensitive information.
Secrets are helpful for addressing the configuration of sensitive data such as passwords, tokens, and keys without exposing these sensitive data to images or pod specs. A secret can be used as a Volume or as an environment variable. With secrets, it is easier to process strings that contain sensitive information.
Creating a Config Map¶
From the main menu, select Container > Config Maps.
Click New Config Map and provide details for the following.
Name: Enter a name for the config map.
Application: Select an application that requires the config map.
Environment: Select the config map usage environment, for which dev, alpha, beta, ppe, and prod environments are supported currently.
Cluster: Select the cluster where the application is deployed. Note that the cluster is already pre-configured by the system.
Enter the Config Map information (Key/Value pair) that needs to be configured, or upload a file with the filename as the Key. The size of the file should not exceed 1MB.
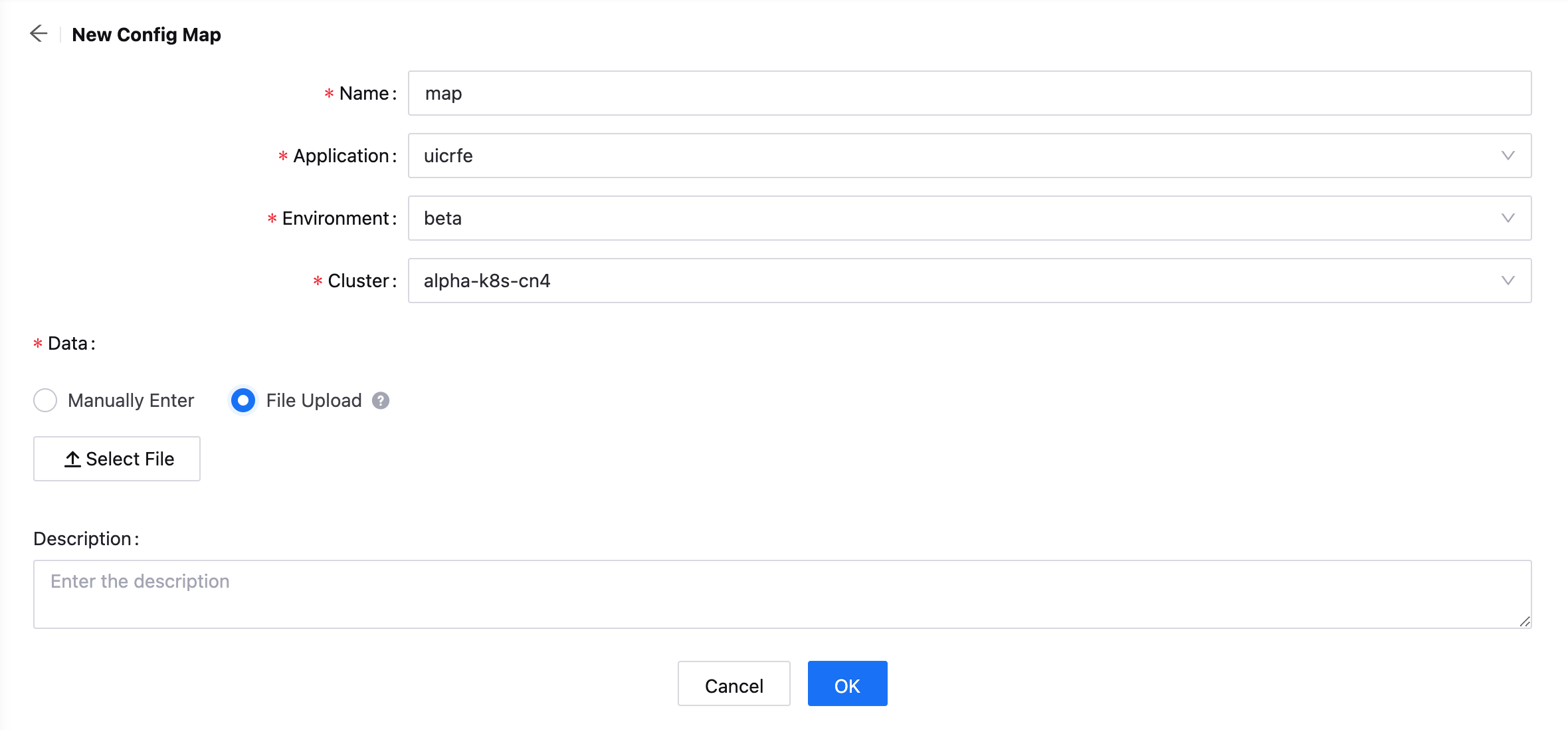
Enter the description for the config map.
Click OK to complete the configuration.
Creating a Secret¶
Select Container > Secrets.
Click New Secret and provide details for the following.
Name: Enter a name for the secret.
Application: Select an application that requires the secret.
Environment: Select the secret usage environment, for which dev, alpha, beta, ppe, and prod environments are supported currently.
Cluster: Select the cluster where the application is deployed. Note that the cluster is already pre-configured by the system.
Select the secret encryption type: Opaque or kubernetes.io/rbd
Opaque: Secret in Base64 encoding format for storing passwords, keys, etc.
Note
The value of the Opaque type needs to be filled with Base64-encrypted content. You can use the online encryption and decryption tool: https://www.base64encode.net/.
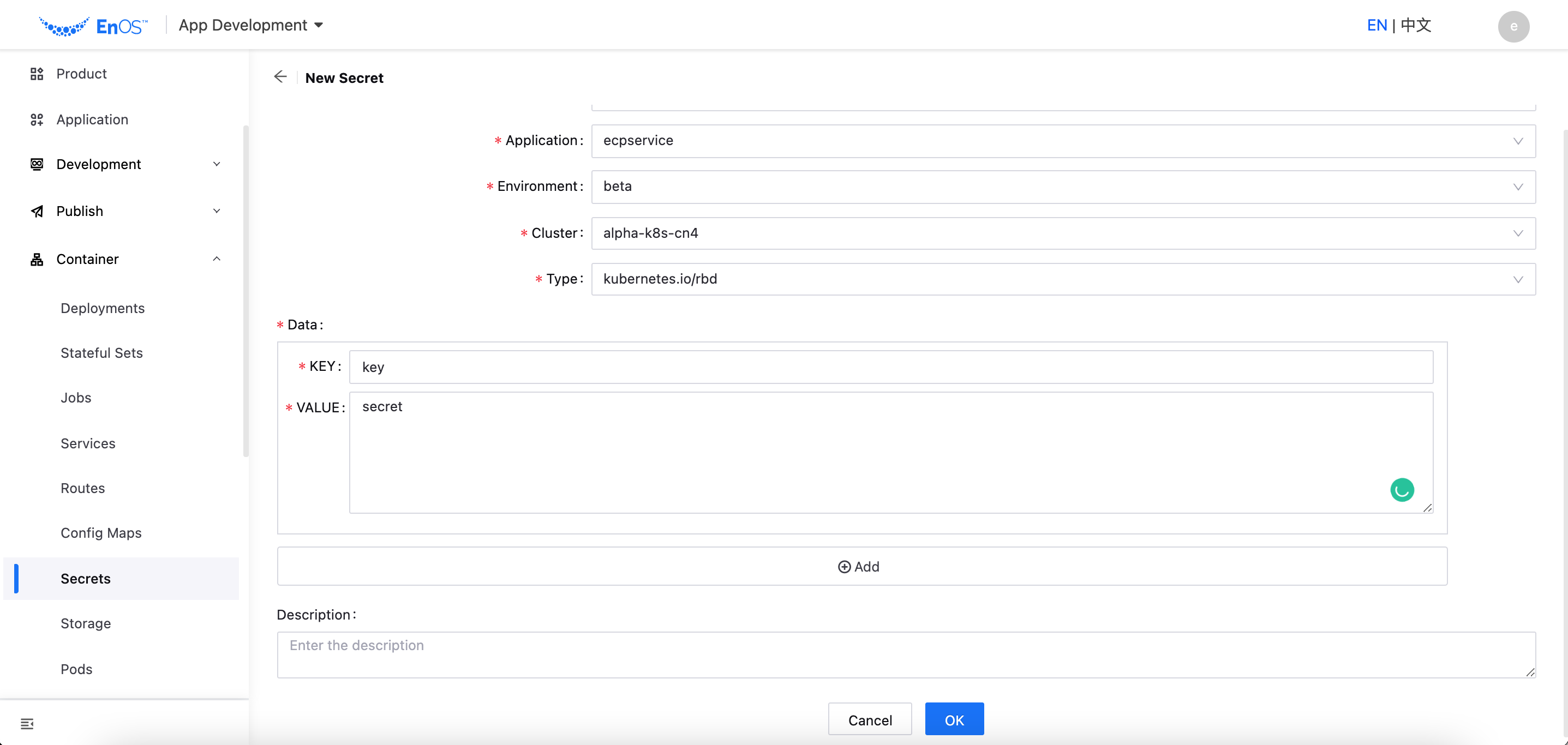
Enter the Secret information (Key/Value pair) that needs to be configured.
Enter the description for the secret.
Click OK to complete the configuration.
Next Step¶
After the Config Map and Secret are created, you can edit the corresponding Config Map and Secret in the Deployment configuration of the application.
After the config map and secret are created, you can clone, edit, and delete them as needed. The specific steps are similar to those for Configuring Deployments.