Device Connectivity Overview¶
The connection scheme is usually selected according to the hardware capabilities of the device and the security requirements for the device connection.
Before being connected to the IoT, the object must first have the ability to be connected. In other words, the following requirements must at least be met:
Can be connected to the network.
Supports the burning of firmware and running of connection programs.
According to the above, devices in the real-world can be divided into two major categories:
Smart devices: Support firmware burning, as well as direct connection to the IoT platform via Wi-Fi, GPRS, 3G, or 4G signals. A smart device can directly connect to and communicate with the IoT Hub to complete authentication and data transmission.
Non-smart devices: Do not support firmware burning, and lack the ability to connect to the IoT platform via Wi-Fi, 3G, or 4G. In this scenario, the devices need to connect through an edge gateway that is able to support firmware burning and network to the IoT platform. The data of these devices are then collected by the edge gateway. The device connected via this solution is also called the sub-device. The gateway serves as a proxy of the sub-devices to help them complete operations such as authentication, login, and data transmission.
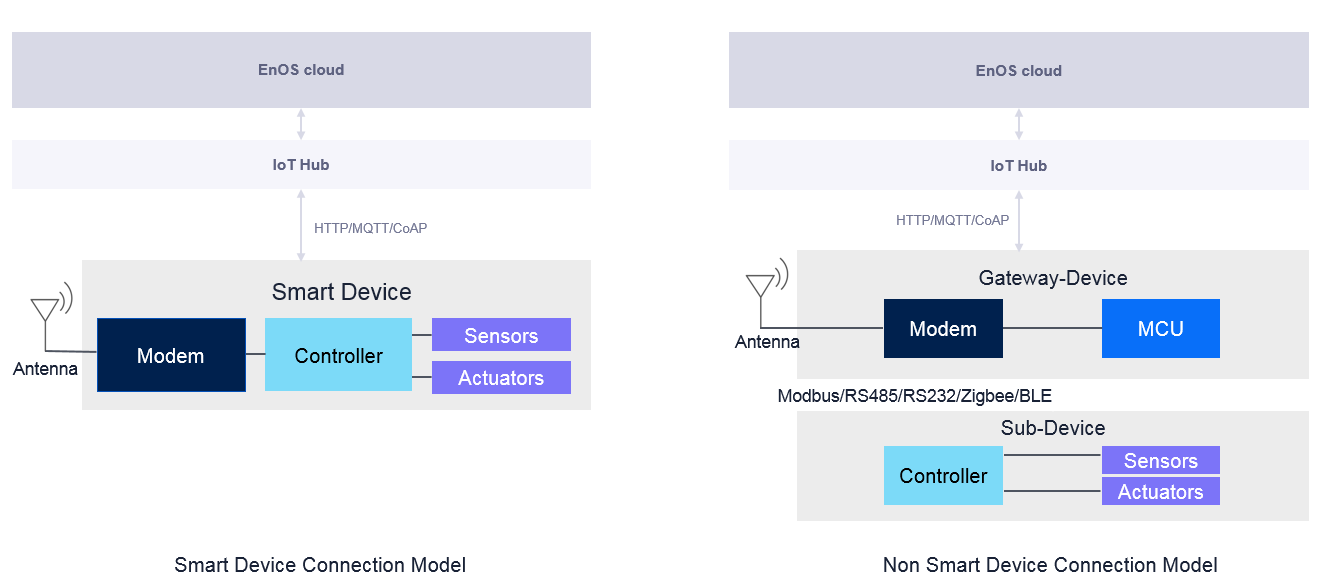
Smart Device Connection¶
Smart devices can be connected directly to the cloud. Some common devices include:
Devices with smart acquisition rods, such as household inverters, and household energy storage batteries.
Smart home devices, such as surveillance cameras, and smart thermometers and hygrometers.
Non-Smart Device Connection¶
These devices need a gateway proxy to connect to the cloud. Some common devices include:
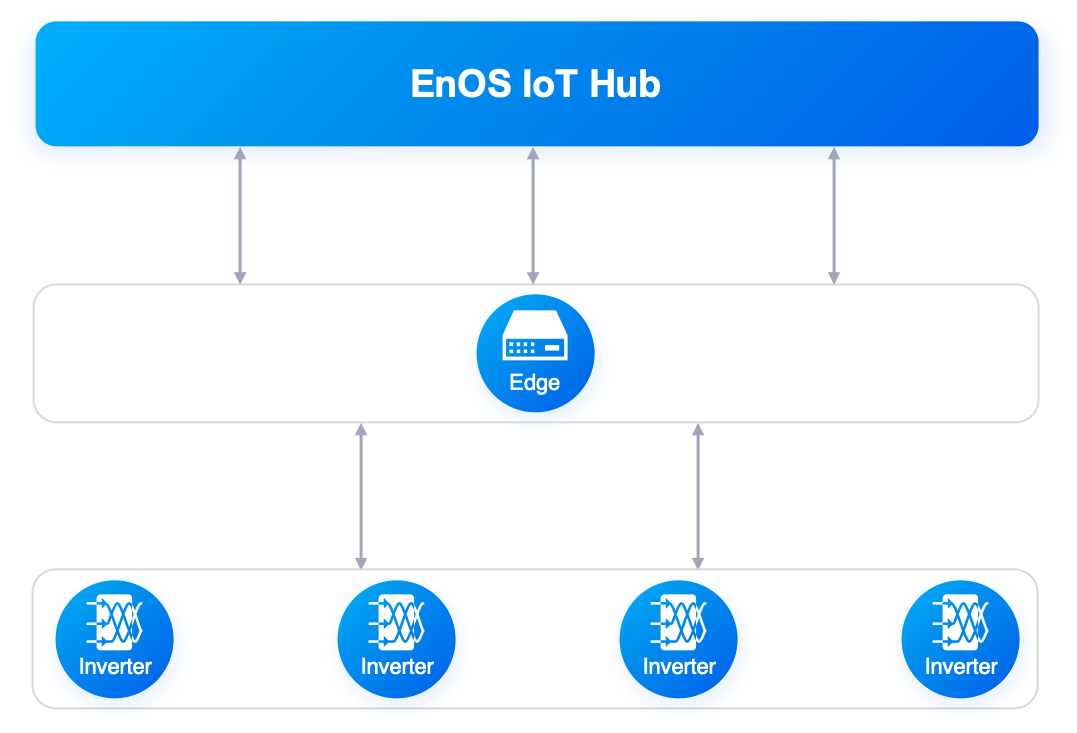
Distributed inverters: the gateway collects data directly from multiple inverters and then sends the data to the cloud.
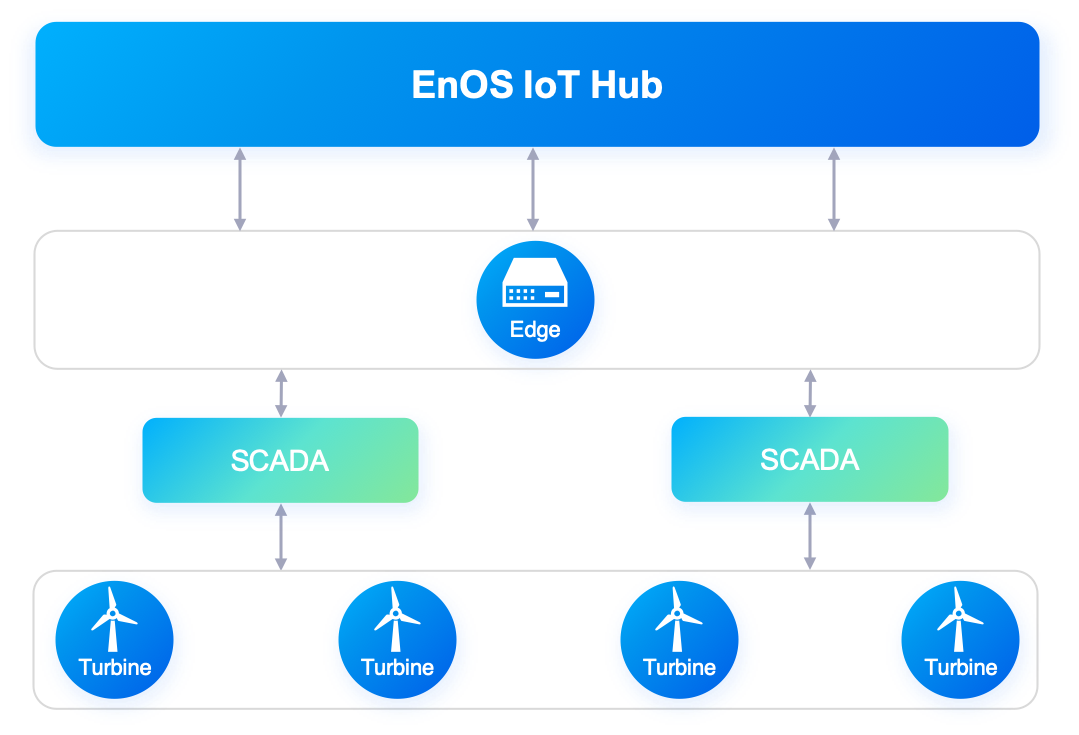
SCADA: the SCADA is connected directly to the wind turbines and collects their data. The gateway in turn is connected to the SCADA to collect the data, and then sends the data to the cloud.
Security Authentication Options¶
The EnOS IoT Hub supports two security authentication methods:
Secret-based one-way authentication: one-way authentication, relatively weak security, enforced by the system by default.
Certificate-based two-way authentication: two-way authentication with high security, enabled by the user.
For more information about the authentication mechanism for device connection security, see Device and Cloud Security.