Creating your Certificate Signing Request (CSR) File¶
To obtain an X.509 certificate from the EnOS CA, you need to create a CSR file in your device or application.
The following procedure uses OpenSSL as an example to create a CSR:
Generate a key pair.
openssl genrsa -out <key_name>.key 2048
Note
You MUST use RSA algorithm with 2048 bits to generate the key pair.
<key_name>is the name of the key, for example,deviceCert.key.Create a CSR for your device or application.
openssl req -new -key <key_name>.key -out <csr_name>.csr -sha256
Note
The
<key_name>.keyfile is the key that you generated in step 1 and<csr_name>is the csr file name, for example,deviceCert.csr.Provide information for the following.
CSR file information¶ Subject Field
Mandatory?
Description
Max Length
Corresponding Initials
Country Name
Yes
The country code. For the specific country code, see Country code
2 characters
C
State or Province Name
Yes
The state or province name, for example, Guizhou
64 characters
ST
Locality Name
Yes
The locality name, for example, Kaili
64 characters
L
Organization Name
Yes
The organization name
64 characters
O
Organizational Unit Name
Yes
The department name
64 characters
OU
Common Name
Yes
The certificate common name. When applying for a new certificate, ensure that the common name is unique; it cannot duplicate the common name of any existing device or application.
64 characters
CN
Email Address
No
Email Address
64 characters
EA
Note
There might be times when information for fields other than the ones listed in the table needs to be provided. When this occurs, you can press enter directly to skip it.
When updating the certificate for an existing device/application, use the Common Name in the old CSR.
The system administrator can view the details of the CSR request in the EnOS Management Console. Upon logging in, go to System Management > Certificate Management.
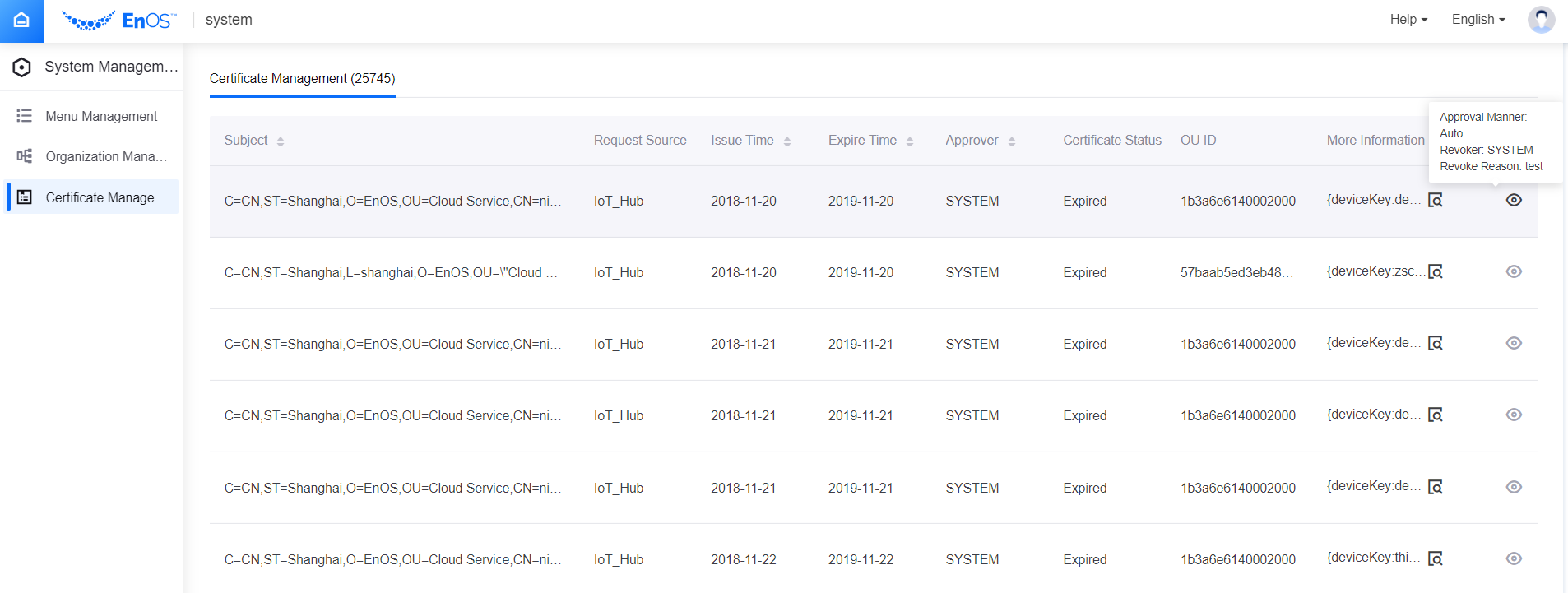
Subject: The subject of the X.509 certificate, which consists of attribute-value pairs from the subject fields in the CSR file information as per the table above. You can either mouse over the text or drag and expand the table column width at the header to see the full information.
Request Source: The source that directly invoked the certificate service.
Issue Time: The start of the certificate validity period.
Expire Time: The end of the cerficate validity period.
Approver: The approver who issued the certificate.
Certificate Status: The current status of the certificate, namely Valid, Expired, or Revoked.
OU ID: The organization ID which the asset belongs to.
More Information: The device key and product key of the asset.
To view the manner of approval, the person who revoked the certificate, and the revoke reason, hover your mouse over the icon on the right.