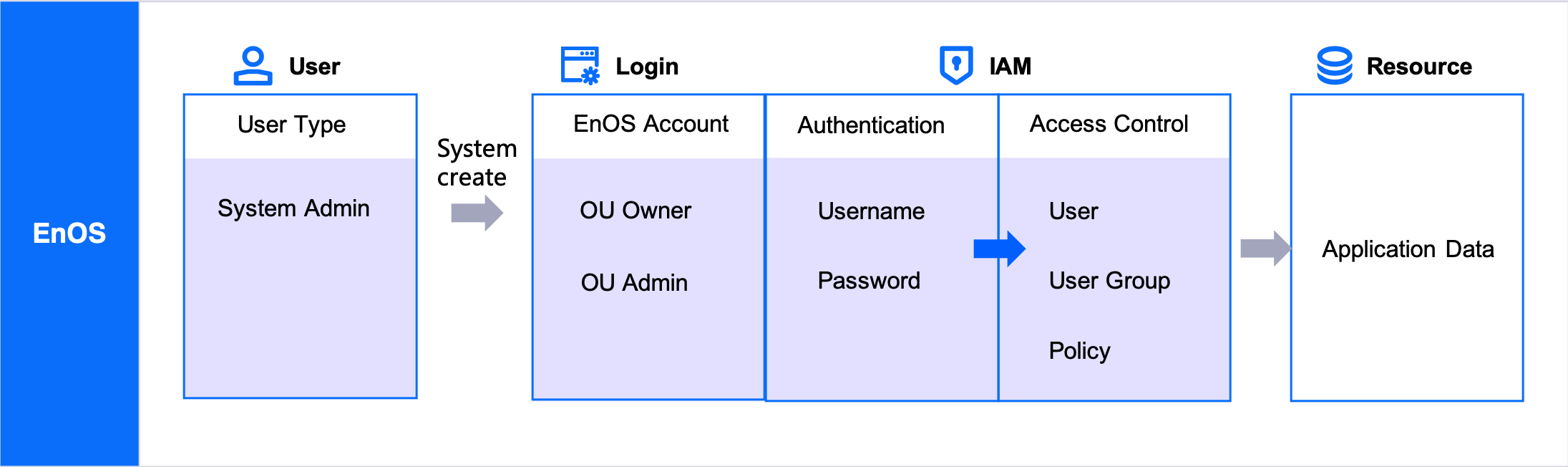
Organization, User, and User Group¶
The user administration hierarchy can be divided into the following, from top to bottom:
Organization
User
User group
Organization (OU)¶
In EnOS, resources are segregated by OUs, where an OU is the top-level management unit with a collection of user accounts, assets, etc.
Through IAM, you can centrally manage all users and check user activities within this OU. Each OU has a unique master account called OU owner and other types of user accounts. The OU owner can control the access rights of other users through the binding of corresponding access policies.
User¶
You can create multiple users within an OU. Each user account has its own credentials (username and password) to log in to EnOS Management Console. User authorization is accomplished by assigning the appropriate policies to the user.
The user accounts in EnOS can be divided into the following types.
System Administrator¶
A system administrator is a user with OU owner permissions under an OU named “System” (a user with OU owner permissions under other OUs are not system administrators). Each EnOS instance has one or more system administrators.
For public cloud, the system administrators are the EnOS administrators.
For private cloud, the system administrators are usually the designated staff of the customer’s organization, who are responsible for managing the user accounts and resources at the corporate level.
The system administrator can create OUs and have access to the system configuration, such as customizing the navigation panel and manage the lifecycle of organizations in the system management menu.
Key Capabilities¶
Menu customization
Create and manage the menu items or import the menu items in JSON format.
Synchronize the sequence and ID of the menu to IAM for authorization purposes.
Organization management
Create an organization with the information of the organization and owner. You can also assign an administrator for this organization.
Manage organization, reset password of the OU owner, and authorize the applications to an organization.
Certificate management
View the details of the certificates used in EnOS Clou.
For more information, see X.509 Certificate Service in EnOS.
OU Owner¶
When a new organization unit is created in a cloud instance, a master account called OU owner is generated for the OU. The OU owner has complete, unrestricted access to all resources in this OU, including the access to the IAM module. The OU owner can create accounts for other users and authorize the users under this OU.
OU Administrator¶
The OU owner can create one or more OU administrators. An OU administrator is the user who has been assigned the built-in policy administrator which has full access and management privileges, in particular, the access to IAM module. The OU administrators can manage the lifecycle of users, manage the organization information and accounts, and grant access policies for users.
Key Capabilities
Creating a User Account in an OU
Create an individual user and grant policies. For more information, see Creating a User Account in an OU.
Managing the Organization Information and Organization Accounts
Manage and maintain the organization information and change the organization owner.
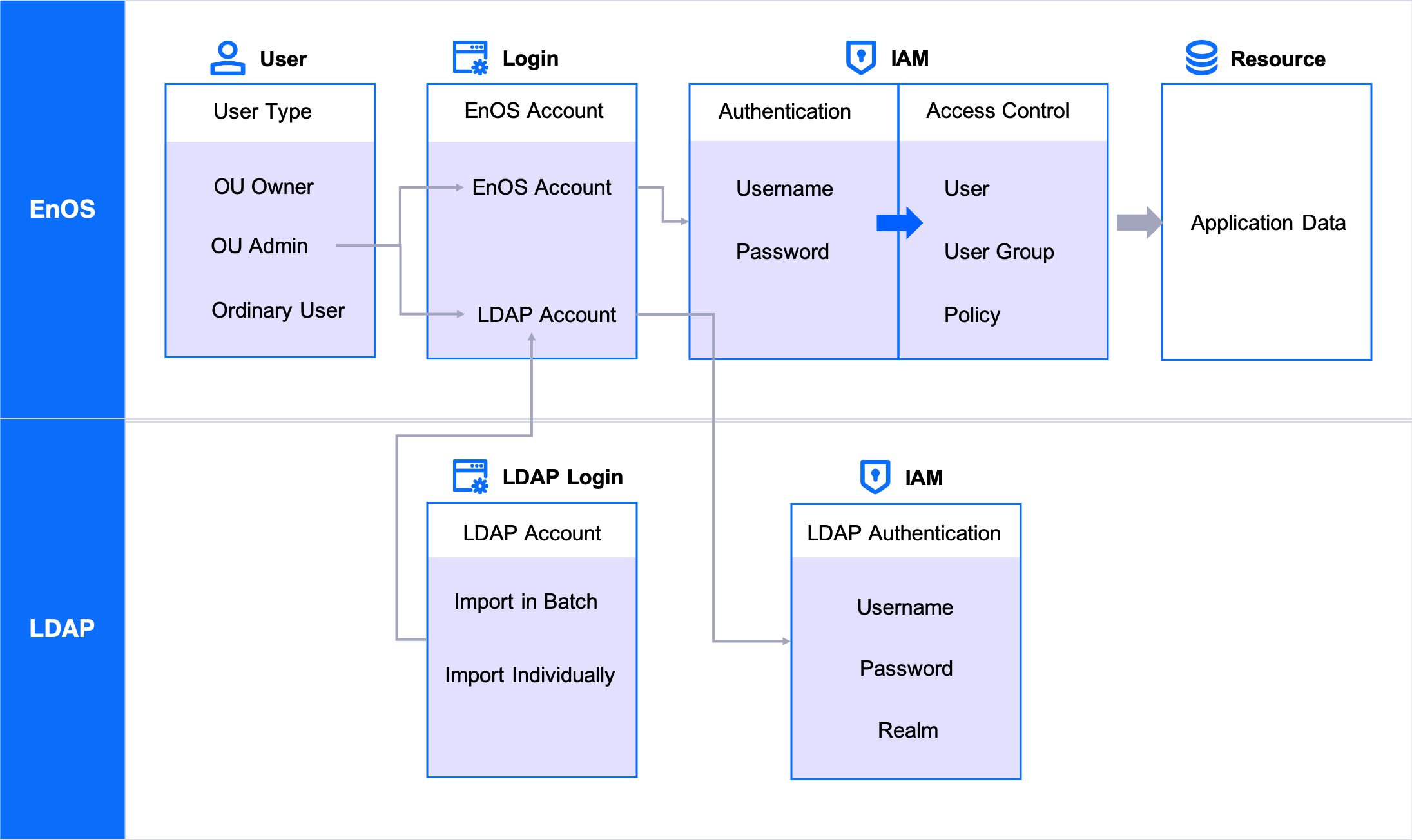
Manage LDAP users
EnOS supports the synchronization of users from an LDAP directory to EnOS user account system and grant permissions for these LDAP users. For more information, see LDAP Federation Overview.
Manage Single sign-on Users
EnOS SSO service is used to solve identity authentication issues between EnOS system and different business applications, where users can use one login to access different applications. For more information, see Single sign-on.
Ordinary User¶
An ordinary user is one who has access rights that are just sufficient enough to complete their job responsibilities on EnOS. The OU owner or OU administrator can create users and assign access policies for them.
Ordinary users are divided into different types according to their source and organization.
Internal user: An internal user is created and can be managed natively within an OU. The user can be given access permissions through being added into user groups, or assigned policies directly. The OU administrator can create, edit, delete, change user passwords, assign access permissions, etc. for the user.
External user: An external user belongs to another OU, and are added to the OU to use the OU’s resources. In EnOS, certain user accounts might need to work across organizations to perform IoT implementation and development. For example, you can import an operation staff, who is created in another organization, into your current organization. Such users can be assigned appropriate access rights in different OUs. The OU administrator can add, remove, assign access permissions, etc. for the user.
LDAP user: An LDAP user is create automatically once the user logs in to EnOS through LDAP and the user’s information is imported through LDAP federation. The OU administrator can only delete and assign permissions for the user. For more information, see LDAP Federation Overview.
SSO user: An SSO user is created automatically once the user logs in to EnOS through SSO, and can access all trusted applications after a single authentication. The OU administrator can only delete and assign permissions for the user. For more information, see Single Sign-On.
If a user is not deleted from SSO, but is deleted from the list in EnOS Console Management > SSO, the user will be created automatically (added back to the list) along with the user details, but the previous access permissions will be gone, and the OU administrator will need to reassign the permissions.
User Group¶
A user group is a collection of users. The user group helps you centralize the management of the users who perform the same tasks in EnOS. The policies assigned to a user group are applied to all users that belong to this group.
All types of users ( internal user, external user, LDAP user ) can be added to a user group.
You can create user groups and define access policies according to the business scenarios. For more information, see Centralizing Authorization by Grouping Users.